What happens when you negotiate with a hacker?

Clients have a tough choice to make when they’re hit with a ransomware attack — to pay or not to pay?
“If you decided not to pay the ransom for whatever reason, and that hacker ultimately discloses that information, what does it open it up? What opens up for contractual liability or just reputational harm?” John Farley, managing director of cyber at Gallagher, poses in a webinar Wednesday.
In Gallagher’s cyber insight session, What Really Happens When You Negotiate with a Hacker: An Insider’s View, Farley and Evgueni Erchov, head of security research and strategy at Arete, use simulated voicemails to walk attendees through a ransomware negotiation scenario.
“We’ve hacked your company recently and now we have over 100 GB of your company’s data. It’s encrypted on your servers and downloaded to our server….no one in the world would know about the leak from your company until we will finish our negotiations with you,” the hacker says, and demands $1 million in Bitcoin to be paid within five days.
Erchov says communication with a ransomware attacker begins via email, or increasingly via chat forums on the Tor browser (a browser that attackers choose because it hides their real server address).
As the simulation continues, the hackers prove they are not bluffing by showing the company their private data. They promise not to publicize it if the company meets their demand. “As a bonus,” the hacker says they will give the company a decrypter and a “backdoor access protector so no one can hack you again in the future.”
This is a situation of double-extortion, Farley says, since the hackers have both exfiltrated and encrypted the company’s data, so that they can’t access it until the demands are met.
“Probably close to 70% of cases nowadays involve data exfiltration along with the encryption,” Erchov says.
When attackers request Bitcoin, Farley says it is more likely the forensic investigator will have immediate access to it. That helps to deploy payment, and insurance policies are designed to reimburse the costs.
In the simulation, the CFO of the breached company says, “We are going ahead with the extortion payment, but $1 million is a heck of a lot of money. I say we try negotiating with a lowball offer… offer $10,000 in Bitcoin and let’s hope they go away quietly.”
What Really Happens When You Negotiate with a Hacker: An Insider’s View, Gallagher.
Hackers will typically negotiate a ransom demand down by an average of about 70%, depending on the scenario, Erchov says. “They always expect that the initial demand is pretty much not going to be paid.”
For example, if backups of the data are available, “we have to negotiate only for [the] promise of data deletion. It gives us additional leverage since we don’t need a decryption, or potentially in some cases, we don’t even need to pay anything,” Erchov says.
As the simulation continues, the company begins to question the legality of giving into the ransom — in entities sanctioned by the U.S. Office of Foreign Assets Control (OFAC), it is prohibited by law to pay hackers.
Erchov says his team will run through an OFAC compliance process to determine if the hackers are based in a location where ransoms are illegal. If they find the attackers are on the sanction list, “legally, we will not be able to facilitate the payment.”
As the simulation goes on, the hacker devolves into triple extortion by reaching out to the company’s major client and threatens to release their data first if the company doesn’t pay.
Erchov says this is a new tactic they’ve observed in the last year.
“That’s why it’s really important to have a team of not only the incident responders, forensics company, but also breach coaches [i.e., a law firm that specializes on privacy laws between clients],” Erchov says. “They play also a critical role to provide additional information to the clients that you then have to make a business decision on whether they want to pay or not.”
When the negotiation closes, Erchov says hackers follow through with their promise to return company data. “If they’re very well-established, they in a sense think of themselves as a business and they do care about the business reputation.” However, they typically have a provider run through “dark web” servers to ensure the data doesn’t show up anywhere.
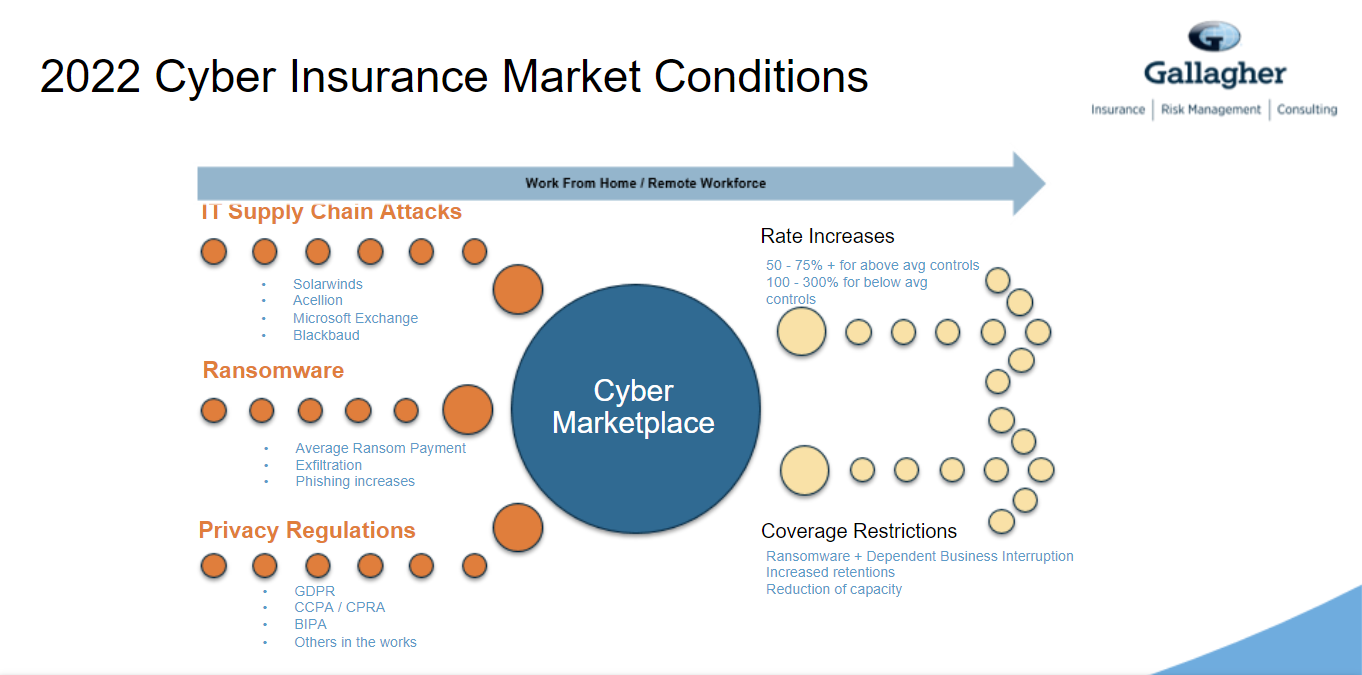
Farley says the cyber hard market is making underwriters “nervous for good reasons…We’re seeing six- and seven-figure demands. Those lead to limit losses for carriers.”
He notes that IT supply chain attacks, ransomware increases and privacy regulation have all resulted in rate increases and coverage restrictions.
What Really Happens When You Negotiate with a Hacker: An Insider’s View, Gallagher.
Farley emphasizes the importance of having controls in place to mitigate ransom risk. Multi-factor authentication, employee phishing training and endpoint detection are key.
“[Insurers] also want to see that you have patch management in place. So, a written and ordered plan to address the zero-day vulnerabilities that may become known; the hackers realize that they can exploit,” he says.
Feature image by iStock.com/mikkelwilliam





